What is Zero Trust and ThreatLocker?
Zero-Trust is a security framework which states that systems should never trust any entity inside or outside of the organization, at any time. Only permitted applications and files will be allowed to run on your computer endpoints.
ThreatLocker ensures that all apps, files and services on a computer have prior authorization to run, and their permissions are ring-fenced with what they’re allowed to do. Basically – NO applications are trusted and cannot run unless they have been preemptively given explicit permissions and guidance on what they’re allowed to do. This is called whitelisting and ringfencing.
When an App is Blocked

This is an example of a notification you will see when Threatlocker stops an application or process from running. If you do not recognize the application attempting to run, you can safely ignore the notification or click Don’t show again, because we periodically review all blockages for any potentially unwanted programs or processes on all computers. If the application is something you are trying to run, you can click on the Request Access button to send us an immediate notification.
Submitting App for Approval
When you need an app to be allowed to run, just hit the Request Access button. Our system will automatically triage the alert, and spring an engineer into action to vet the app and make a determination on approval. In most cases, you will just receive a notification on your desktop that your app is ready to run.
In some cases, we may need some additional information in order to approve the app. It entirely depends on the process or application, but sometimes we may need to schedule a time to facilitate a proper install. Please be sure to include a detailed description of the application and its purpose.

Keep an eye on your email as we will send you updates on your application request ticket there, and we may ask for additional information to process your request.
Scheduling Ahead of Time
If you know that there is an update needed for an application you use, schedule it with us! Send us a ticket to support@umbrellaitgroup.com and we will create a remote service call to set up your new application correctly.
Threatlocker Features and Updates
Threatlocker now features more than just Application Whitelisting and we have much faster response times than ever before. For all customers, all Threatlocker requests are actioned within 15 minutes, 24/7.
Automatic Elevation
This is a feature of threatlocker where for certain applications, you should no longer need an administrator to enter their password or approval to run an the application. Things such as Quickbooks Updates can now be run automatically, and Threatlocker will grant administrative access for updates, without having to go through an approval process by Umbrella. Simply click on your applications icon and let it run!
Web Control
A new module called Threatlocker Web Control has replaced DNS Filter Agents. This module filters certain parts of the internet that are not safe for work or could be considered malicious. You may see an option to request access to a web page.
Cloud Control
This module is discussed in-depth as part of our Microsoft 365 Hardening Service, but in short, this service creates an allow-list for IP Address locations for all users, instead of the typical limitation of just “United States”. This makes access to Microsoft 365 significantly safer without adding a bunch more hoops to jump through.
Cloud Control is not be enabled by default for existing uConnect Customers, as it requires a bit of configuration, user training, and tuning to get just right. For a typical organization, the price is around 4 hours of project labor to enable. For new organizations joining uConnect Advanced Security or implementing a Microsoft 365 Hardening Project, Cloud Control will be included.
We are currently offering a promotion to enable Cloud Control! Please reach out to Umbrella via the IT Portal if you would like to get started.
Threatlocker Mobile App
The Threatlocker mobile app is a non-intrusive service that will run in the background on your phone to verify your identity when you try to sign in to Microsoft. It’s an extra layer of security to ensure nobody can log in to your account, even if they have stolen your credentials and MFA token. It’s super easy to activate and will not get in your way, while providing a huge benefit to your overall organizational security.
Get Started
You received a text message that looks similar to this:
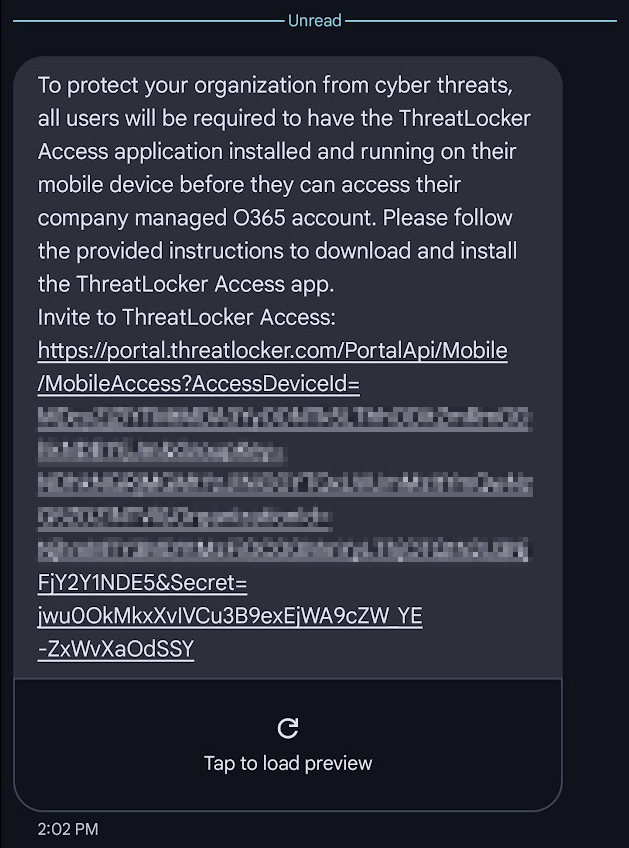
Great! Click the link and it should lead you to the app store where you can download and install the Threatlocker App (iPhone) or Threatlocker for Android
Install download and install the application.
Once the app is installed, go back to the same text message from above and click it again. This time, instead of taking you to the App Store, it should open the app and say “Welcome to Threatlocker” at the top.
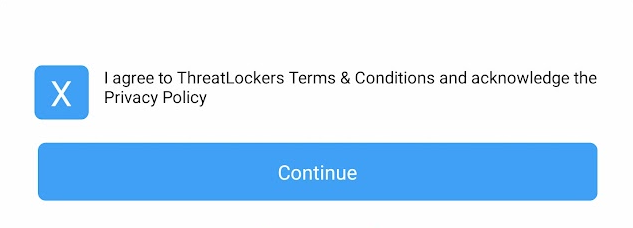
Accept the Threatlocker Terms and Conditions, and hit Continue.
Next, we have to allow all the permissions required by Threatlocker to work correctly. The app will walk you through enabling all the required permissions.
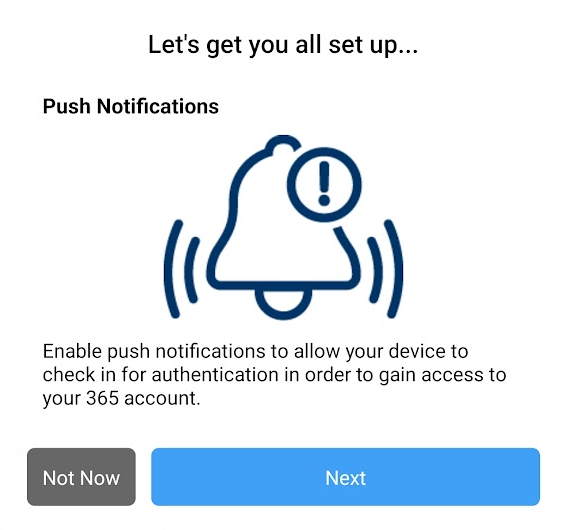
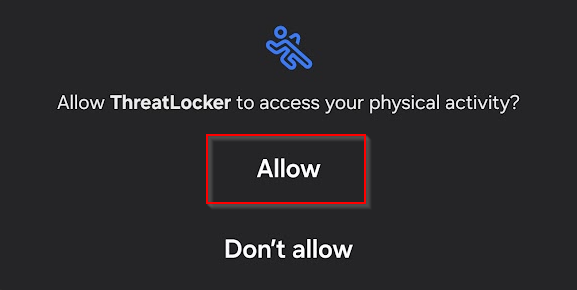
Ensure to click Allow for all the requested permissions.
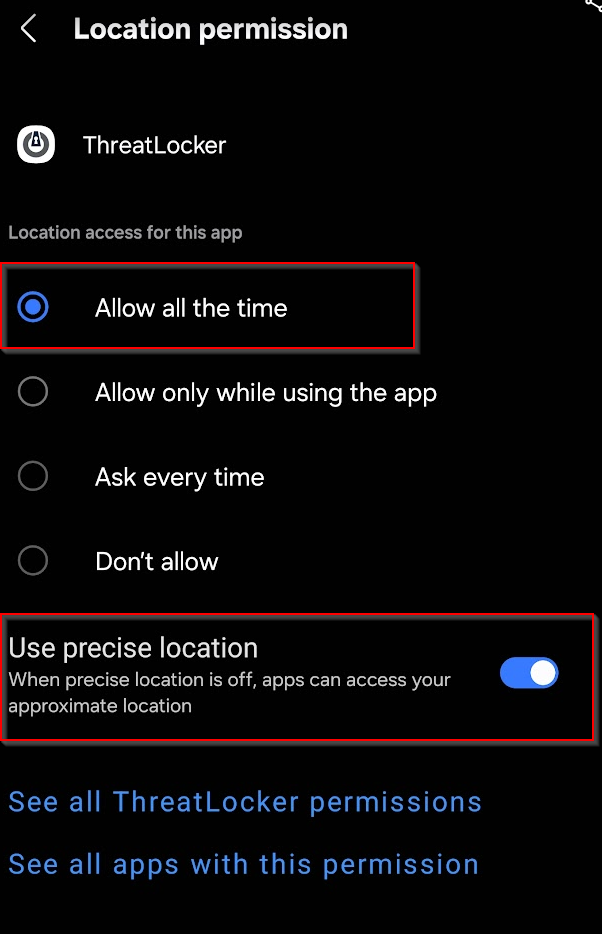
On some phones, you may need to go into the settings to grant more specific permissions. Make sure to choose Allow all the time instead of other options, and allow Precise location usage.
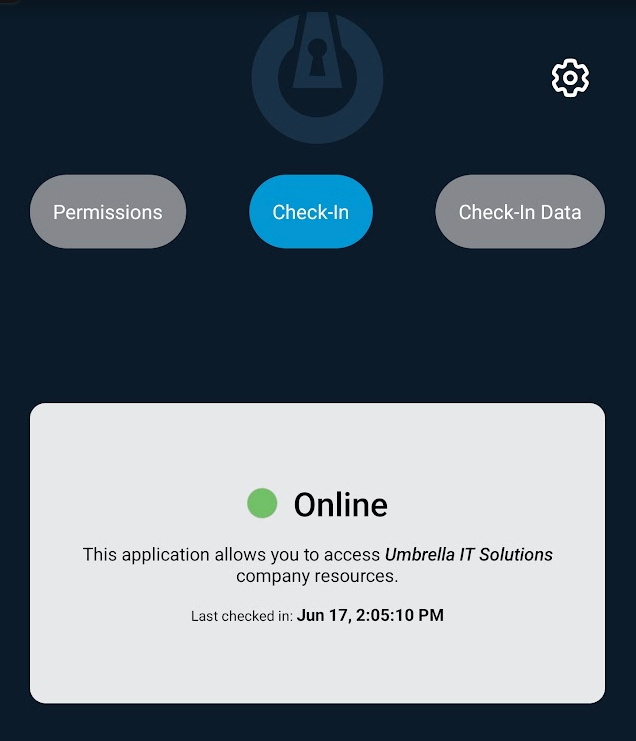
Once you see this Online screen, you are all set and everything is configured correctly. Thank you for helping keep your organization secure.